WWW.ipcainterface.com login as it is considered to be the main portal for users who have to access their IPCA Interface and use internal assets in computer systems that function efficiently. As an employee, admin or active partner, knowledge of how the login system works is important for all-day activity.
The “digital-first” world we live in requires a focus on centralized portals to manage data, workflows and communication for organizations. ICPA Interface login module is created with an intention to offer limited and role based accessibility while maintaining the data secrecy and work clarity. And that’s why our guide covers everything you need to know about how the login process works, the features it powers, popular issues and some best practices – all in simple and straightforward terms.
Read Also:- QuillBot AI: Complete Guide to Features, Benefits, and Use Cases
What Is WWW.ipcainterface.com Login?

WWW.ipcainterface.com login is a secure web-based authentication system that allows authorized users to access the IPCA Interface platform. This portal is commonly used within enterprise or organizational environments where controlled access to internal tools, dashboards, or data systems is required.
The login system ensures that only verified users can enter the platform using unique credentials. It is designed with security layers that help protect sensitive information from unauthorized access. The portal can be accessed through standard web browsers on desktops, laptops, and in some cases, mobile devices.
Key purposes of this login system include:
- Centralized user authentication
- Secure access to internal dashboards
- Role-based permissions
- Activity tracking and compliance support
Who are the IPCA Interface Portal Users?
The WWW.ipcainterface.com login portal is usually for those involved in running an organization that uses the IPCA Interface system. Users may be employees, managers, IT administrators or line workers depending on the organization.
Different users roles likely have different access. For instance, administrators can control access to users and configurations, while common users only can be allowed to access or modify the given information. This gated architecture provides oper ational discipline and data integrity.
Common user categories include:
- Daily tools use by office staff
- Managers looking at reports and dashboards
- IT teams maintaining system settings
- Authorized external collaborators (if permitted)
Read Also:- Improve DH58GOH9.7 Software: Complete Guide to Performance, Stability, and Optimization
Step-by-Step Guide to WWW.ipcainterface.com Login
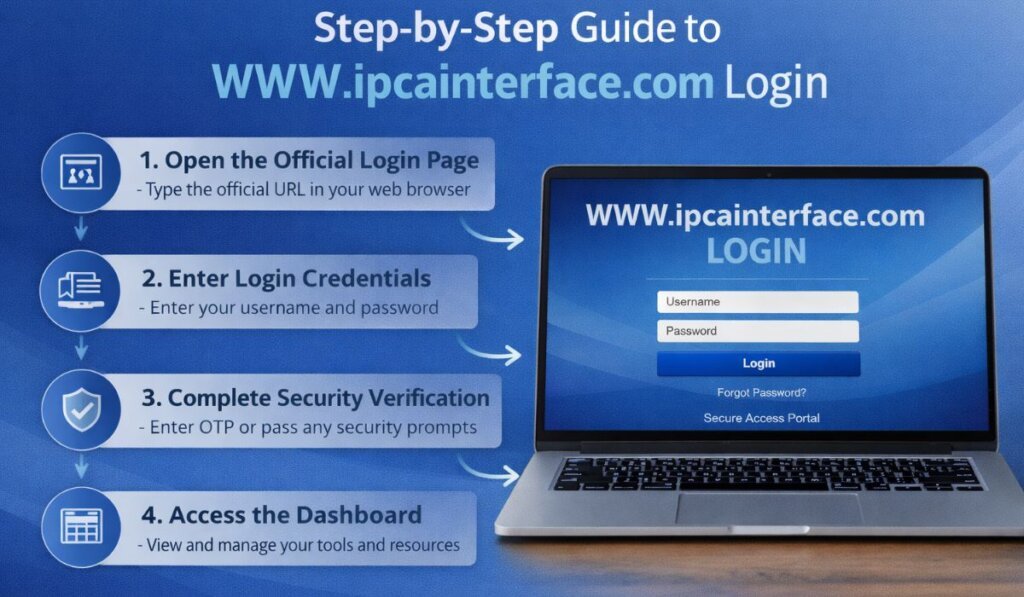
Step 1 – Go to the Official Login Page
Open your web browser and type the official login link received by your company. Double-check the address to avoid any security threat.
Step 2: Enter Login Credentials
You should see empty fields for a username and password. Use the username provided for you by your system administrator.
Step 3: Complete Security Verification
Certain accounts may need to be confirmed through a onetime password or a security alert for the sake of safety.
Step 4: Access the Dashboard
Once you have successfully authenticated, you will be taken to your dashboard and have access to the tools/features that we allow.
This basic flow allows for quick, hassle-free entry to the system when required on a daily basis.
System Requirements for Smooth Login
To ensure a smooth WWW.ipcainterface.com login access, users should meet minimum System Requirements. It is web-based making it generally unnecessary for special software.
Recommended requirements include:
Recent web browser (Chrome, Edge or Firefox)
- Stable internet connection
- JavaScript and cookies enabled
- Secure device free from malware
By fulfilling these conditions, one can prevent a number of login issues and performance problems.
Key Features After Login

Once you complete the WWW.ipcainterface.com login users are able to have access to some of the most crucial features according to their levels. All of these characteristics are intended to streamline processes and bring practices together.
Dashboard Access
Dashboard – At a glance information – The dashboard itself immediately shows key actions, updates or system notifications relative to the user.
Data Management
Data Management of the information flow between users can benefit from viewing or modifying data according to certain permissions.
User Role Controls
User access is narrowly defined by role, limiting exposure to unauthorized browsing or searching.
Secure Session Management
Sessions are watched and automatically invalidated on inactivity to secure the sensitive data.
Benefits of Using WWW.ipcainterface.com login
There are numerous benefits provided to organizations and individuals through the login system. It’s more organized and it promotes efficiency, safety and accountability.
Major benefits include:
- Centralized and secure access
- Reduced dependency on manual processes
- Improved data protection
- Auditable and transparent trails and access logs
- Consistent user experience across departments
This advantages allow the platform to perform reliable operations over a long operation period.
Common Login Issues and Their Solutions
There are times even a good system can have some issues with logins. Common problems can be explained, so users should receive quick help.
Incorrect Username or Password
This is the number one problem. Remember to verify credentials and take caps lock off.
Forgotten Password
Select the ‘password recovery’ option and enter your new password or consult your system administrator.
Browser Compatibility Problems
Clear the browser cache, or attempt to log in through another supported browser.
Account Locked
Incorrect password entries will result in an optional temporary ban. This can generally be fixed by either waiting or you could seek help from IT support.
Security Measures in WWW.ipcainterface.com login
The IPCA Interface log in system has been designed with security as a priority. There are a number of measures to ensure the security of users and organization data.
Security measures often include:
- Encrypted login sessions
- Role-based access control
- Automatic session timeouts
- Login attempt monitoring
These steps help mitigate potential data breaches and unauthorized logins.
Secure Login Guidelines and Best Practices
For the secure use of the WWW, it is important that users adhere to a few security recommendations of WWW.ipcainterface.com login portal.
Best practices include:
- Never sharing login credentials
- Using strong and unique passwords
- Logging out after each session
- Avoiding public or unsecured networks
By taking these steps it can help not only to protect you, but also your company.
Password Management Guidelines
We all know effective password management is key to account security. Passwords should be reset periodically and not follow predictable patterns.
Strong password tips:
- Mix up the letters, numbers and symbols.
- Avoid personal information
- Change passwords periodically
- Do not reuse old passwords
These are practices that dramatically minimize the security risk.
Mobile and Remote Access Considerations
In some setups, WWW.ipcainterface.com login could be proxied into other locations. This provides more freedom, but also makes things riskier.
Remote users should:
- Use trusted devices only
- Ensure secure internet connections
- Don’t save passwords on shared computers
Responsible use maintains secure remote access while safeguarding the data.
Role of administrators in the management of login
Admins contributed a lot for the health of the login system. They deal with the creation of users, permissions, and authorization.
Administrator responsibilities include:
- Assigning user roles
- Resetting passwords
- Monitoring login activity
- Ensuring compliance with internal policies
Efficient management facilitates proper working of the system.
Troubleshooting Advanced Login Problems
For complex issues that cannot be addressed with routine troubleshooting, some technical support may be needed. These problems may be related to system maintenance downtime or server errors.
When facing persistent problems:
- Note the exact error message
- Check system notifications
- Report to local IT support with details
It helps to state the obvious sometimes.
Frequently Asked Questions (FAQs)
What is WWW.ipcainterface.com login login used for?
It is the secure way to log into the IPCA Interface and all functions inside.
Is the portal available to me from all devices?
Yes, provided the device is compliant with basic system and security features.
What are you supposed to do if you forget your password?
Please use a password recovery or contact your Admin.”
Is the login portal secure?
Yes, it is secure in terms of encryption, session controls and role based access.
Why am I temporarily locked out of my account?
Too many mistyped passwords in a short period of time… And you are locked out!
What do you recommend to enhance security of my login?
Go with secure passwords, log out after you use a service and try not to connect over public networks.
Conclusion
The WWW.ipcainterface.com login system is a user friendly and secure access point to the IPCA Interface platform. Knowing how to log in, what the features are, how their login is secure and other tips will give those users uninterrupted access to important tools and information, without compromising security.
The platform is user-friendly while also maintaining a high level of security and features, to be a portal that meets the needs of today’s organizations. With these best practices, users can confidently work with the login system safely as a part of their digital workflow.